Best Linux laptops in comparison
Your perfect Linux laptop: Lenovo or HP – together we'll find it! Imagine opening the box of your new laptop, excited to install Linux on it. Pe...

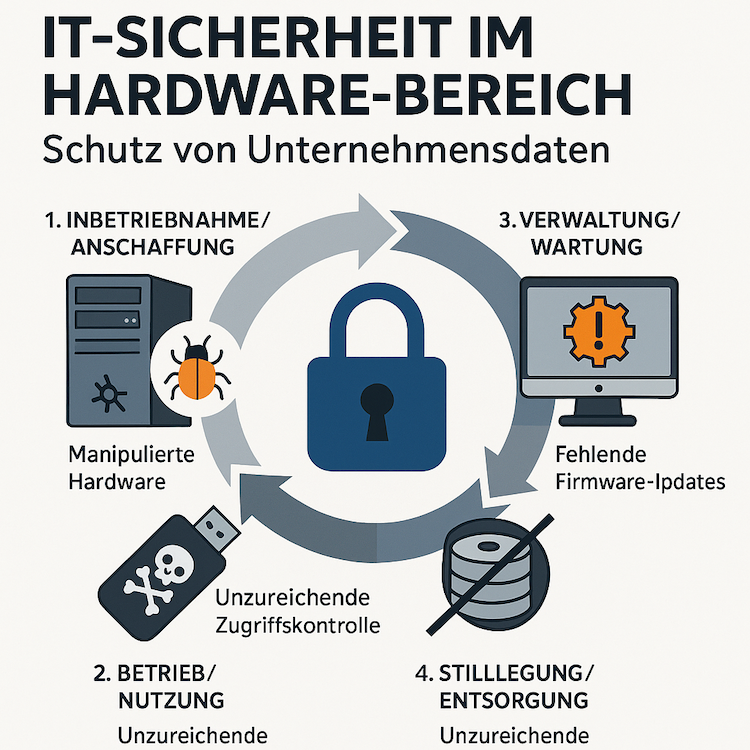
This refers to the protection of the technical components of an IT system from damage, theft, or unauthorized access. To successfully fend off cybercriminals, both companies and users must rethink their security standards. Comprehensive IT security applies not only to software but also to computer hardware. This applies to the entire lifecycle: from commissioning, through ongoing management and maintenance, to the disposal of the equipment.

These are special chips on the computer's motherboard that securely store cryptographic keys used for encryption and decryption. Secure Boot, in turn, is a security standard supported by UEFI that ensures that a computer can only boot a trusted operating system. TPM also controls which operating systems the PC boots. This prevents bootstrap loaders (boot managers) from gaining access to the computer via a malicious operating system.
To optimize their IT strategies and simplify IT processes, companies often rely on cloud infrastructures. Cloud solutions enable virtually all IT areas to be seamlessly and securely connected. To minimize the risk of firmware-based attacks on the hardware technology deployed, the Root of Trust (RoT) concept has become particularly popular. Root of Trust programs such as the Hardware Security Module (HSM) work with special hardware hardening technologies.
These are tamper-proof devices that generate and protect the keys used to encrypt and decrypt corporate data and create digital signatures and certificates. HSMs not only protect cryptographic processes but also enable computer systems and networked mobile devices to verify the authenticity of the information they receive.
 Another cybersecurity solution is RISC-V Security
Another cybersecurity solution is RISC-V SecurityAnother cybersecurity solution to hamper cyberattacks is RISC-V security. RISC-V is often referred to as the computer core, but by default, it is actually a computer bus architecture (ISA) that regulates how software and the CPU interact with each other and which instructions the CPU is allowed to respond to. RISC-V is open-source hardware. This means that the RISC-V implementation, usually under Linux, can be created and run by users at any time without requiring a license or incurring license fees. Since licenses are expensive, RISC-V is a particularly good solution for smaller companies. The free use of the open RISC-V instruction set architecture uncovers architectural vulnerabilities in RISC-V applications and prevents them from propagating into other CPU developments. This makes life difficult for hackers.
Joe Pichlmayr, Managing Director of Ikarus Security Software GmbH, says, "We expect further individualization of attacks this year. Attackers have long recognized that there is much more to be gained with targeted attacks. The CPU vulnerabilities Spectre and Meltdown, discovered in Intel, AMD, Apple, and ARM processor chips, bypass and disable security and encryption methods.
An attacker can exploit this to access sensitive data in kernel memory, such as passwords, encryption keys, emails, etc. Currently, no cases of abuse involving Meltdown or Spectre are known. However, the patches now available significantly impact processor performance. Two other new attack methods were recently discovered: "Zombie Load" and "Store-to-Leak Forwarding." These attack methods affect nearly all current processors in PCs and servers. These new attack methods allow direct access to data or metadata from processes running adjacent to CPUs.
The new EU Network and Information Security Directive, NIS-2-R , establishes criteria for identifying operators of critical infrastructures and defines minimum standards for their information security. The directive has not yet been transposed into national law, but is scheduled to be adopted in 2025. Another standard is ISO 27001, which specifies the requirements an information security management (ISM) system must meet.
ISO certification is the most important cybersecurity certification. It includes a detailed risk analysis as well as the implementation and continuous monitoring of security controls. Effective identification and management of all risks associated with the processing of sensitive data is a prerequisite.
Security threats will continue to evolve in the coming years. To successfully address these threats, a full-stack strategy is necessary, combining hardware security features with software security features.